- The supply of liquid deployment fell sharply for the oblique activation of self -layer.
- Ether.fi dominates the inflow after the upgrade, while other LRTs continue to see.
- $ 2.7b Berachain TVL unlock the volatility of the EVM-based markets on May 6, May.
Despite the profit in general cryptom markets, recent Defi trends show continuous caution among investors and institutions. Data from April 2025, as reported by IntotheBlock, show a reduction in Ethereum amplification derivatives, minimal activity in risky loans and rising stablecoin mining via protocol-controlled mechanisms. A total value of $ 2.7 billion unlocked from Berachain planned before 6 May is expected to further test the liquidity conditions in EVM-compatible networks.
Although the wider market has gathered, high risk loans is hardly specified; Proof that caution still prevails.
Our newest risk recense delves into this and more 👇https: //t.co/yzx6qg4ZSV
– Intothebllock (@intotheblock) April 30, 2025
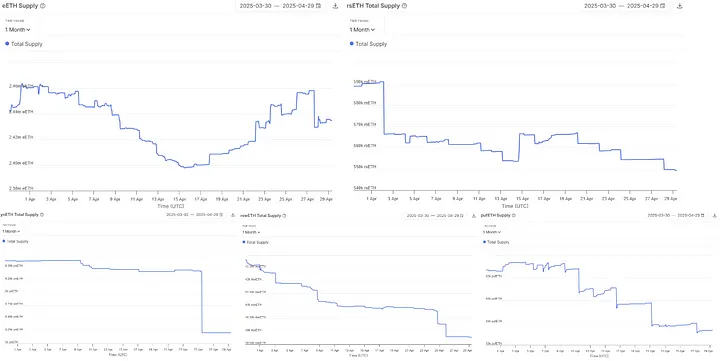
Multiple liquid inputs (LSTs) registered large nutritional reductions in April. The Reth van Rocket Pool experienced the sharpest decrease, which fell from more than 700,000 tokens to less than 600,000 around 7 April. SETH2 and CBETH also fell consistently, with Coinbase’s Cbeth who registered a steep reduction after 10 April.
Wrap Ether (Weth) fell from approximately 2.45 million to more than 2.40 million, while Lido’s Steth started to fall during the middle of the month and then. The Pubeth -Tokken remained fleeting, but finally ended in April on a downward slope.
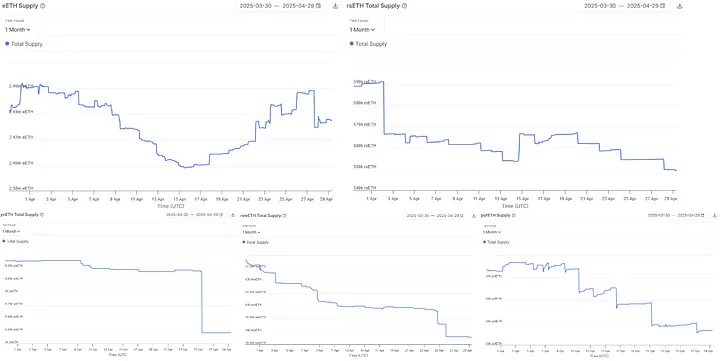
Source: Intotheblock
These shifts reflect on persistent outlets and non -failure about protocols. The trend is in line with user behavior prior to the activation of self -layer of the oblique functionality, which introduced a greater risk of repairing assets. In the meantime, users withdrew tokens, reducing the exposure prior to the upgrade.
Eigenlayer who cuts upgrade changes the LRT distribution
With the successful rollout of reducing, LRT Netflows began to recover. However, the inflow is heavily concentrated in Ether.fi. While other platforms still experience a reduction in the supply, Ether.fi has emerged as a dominant player.
Observers attribute this to the growing liquidity depth of the protocol, which appeals to large participants, including institutions and whales. This asymmetrical distribution emphasizes a shift in the preference for platforms that are experienced as safer or more efficient post-upgrade.
Data on chains indicate that functions with a high risk have not grown, even if crypto-asset prices recover. Bone sizes have remained stable and the liquidation activity has been relatively low in the last two weeks.
GHO Supply reaches new highlights via Protocol -Facilitators
Aave Prime continues to record delivery heights for the GHO Stablecoin. This growth stems from the use of facilitator contracts, such as Lidoghodirectminter, who can not be stunned GHO directly in a Polish mint. The unclaterized tokens are on the market and earn the interest of delivery until they are borrowed.
As soon as a user lends Gho, he is collapsed as if he was beaten immediately. Spark also implements a similar model to expand the stablecoin nutrition, while internal checks are retained. This facilitator -based strategy has made increased credit volumes possible without dependence on external liquidity providers, although it points to the need for robust monitoring mechanisms to manage the systemic risk.
Berachain TVL unlocking signals on the hands of market volatility
A release of $ 2.7 billion in total value will be locked on 6 May of the Boyco hills on Berachain. The event is expected to cause volatility, not only on Berachain, but also in the Ethereum and other EVM networks, given it one of the largest one-day releases in the recent history of Defi. It is expected that such factors such as Slips, APR and strategy capacities will increase in the days after the unlocking due to adjustments to capital allocation.
The number and severity of the attacks on Defi Front ends have increased. DNS -spoofing and social engineering attacks are gradually becoming common because protocols are spread, with third parties that organize onion copies. These attacks are very difficult to identify and defend because they do not use bugs in smart contracts. People always have to check the front -end sources and instead opt for direct contact with the contract.